Hacking
- by Anand
- 5 posts
-
On August 15, Michael Terpin filed a $224 million lawsuit against AT&T. His 69-page complaint claims the telecom giant had failed to protect his phone number—even after escalating his account to a “higher security level” with “special protection”—resulting in a combined $24 million hack of his cryptocurrencies.
This number might dwarf compared to the infamous Mt. Gox hack, where over $460 million was stolen, or the DAO hack ($50 million), or the more recent hacks of Conrail ($37.2 million) and Bithumb ($31 million). But the scary part is the ease with which these hacks are carried out.
In fact, instead of breaking into smart contracts or hacking into exchanges and stealing private keys, now kids between 19 and 22 years old can steal millions at an expense of 99 cents, with relatively no effort.Has blockchain failed to deliver a secure digital currency and has turned into a haven for cybercriminals?Fundamentals of security
The idea behind bitcoin was to create a peer-to-peer system that allowed two parties that did not now and did not trust each other transact financially without allowing for double-spending or hacking the system. For that, it created an immutable ledger that can only break to a “51% attack”—an attack which requires enormous computing power of malicious nodes to overrun the honest ones.
While this system has failed smaller networks, it has been battle-proven with bitcoin, which has not suffered from such blows to date. But no matter how secure a system we design, it will always have one point of failure: humans.
The Heathrow Airport was fined for £120,000 ($155,000) when an employee lost a USB Drive containing 2.5 GB of sensitive files. No matter how secret those files were kept; without proper training and procedures in place, the system can still fail miserably.
Security is a process, not an end state. And our primary enemy is “convenience.” Even the U.S. President is no exception. That’s why we reuse the same passwords on disparate websites or totally abandon them with two-factor authentication. In fact, the AT&T case had nothing to do with blockchain vulnerabilities; the victims had fallen for SIM swapping.
SIM swapping is a technique used by hackers to trick (or even bribe) a telecom operator to redirect the phone number of the victim to the hacker’s SIM card. The hackers impersonate their target by providing fake IDs and claiming they have lost their phone and need their old number redirected to their “new” SIM card.
From there, they can penetrate the target’s email and social media accounts, and extract valuable information about any other account that is insecurely stored there.
For SIM swapping, the hacker only needs to know their target’s phone number, then pull off some social engineering to trick the operator. In an SS7 attack, even social engineering is not necessary, as hackers can use the attack to eavesdrop on SMS messages and steal any PIN codes that are sent to the victim’s phone during a login attempt.
The only way to protect yourself against these measures, for now, is not to use cellphones for authentication—or keep one just for logins and never share its number with anyone.It gets worse
What makes this particularly important for cryptocurrencies is its nature. When hackers steal private data or even healthcare data, they still need to sell those accounts or start exploiting them before they can turn their gains into money—and in some cases, the victims can block those accounts or otherwise minimize the damage.
But with crypto’s, they have immediate access to cash.In some cases, the hackers even ignored the funds they could have accessed in traditional banks. According to REACT Lieutenant John Rose, the attackers “are predominantly interested in targeting cryptocurrencies for the ease with which these funds can be laundered through online exchanges, and because the transactions can’t be reversed.”Who do you trust?
It is interesting to notice the pattern here: hackers attack central locations for gains and hide in the decentralized network for anonymity. In a way, blockchain is accomplishing exactly what it was supposed to do: removing single points of failure and create a network where anyone can trade freely.
As we hear the calls for regulating blockchain, it is also important to remember the primary reason behind bitcoin’s birth: the failure of large central banks, which caused the depression of 2008.
Eventually, it comes down to who do we trust? The central bodies, which are supposed to be the good guys but have sometimes shown they can turn evil, or the masses where hackers and fraudsters can also blend in?
For blockchain supporters, the answer is clear: we cannot hope that the people in power always do the right thing, but we can give the masses more power to take corrective action. In other words, should we opt for a dictatorship and hope we will get a “good” dictator or do we believe democracy always prevails?It comes down to how we use technology. Blockchain has answers in itself.“White hat” blockchain
When the Ghash.io pool got close to controlling 51% of bitcoin mining power in 2014, the community reacted by leaving the pool—so much that the owners had to publicly announce that they “will take all necessary precautions to prevent reaching 51% of all hashing power, in order to maintain stability of the bitcoin network.
”To protect against smart contract hacks, an Israeli cybersecurity startup called Safeblocks has created a decentralized web firewall that protects smart contracts from unauthorized transactions and malicious attacks in real time.
The platform task is to monitor the smart contracts and examine the transaction requests as they come, approving or disapproving them based on the security exceptions the users have set. This way, users can put a limit on the number of transactions per day, capping withdrawals amount of even setting a designated address for withdrawal.
The fundamental idea is that instead of relying on code audits, we have to measure the system in real-time and take action accordingly. This view is much closer to the “security is a process” principle. Only this time, blockchain is a part of this process.
Assessing the breaches mentioned previously, it is clear that blockchain could not have prevented the SIM swapping or SS7 attacks—but it does present a system which is immune to surveillance: dark routing. This technique, as implemented by Mainframe, enables full data privacy, surveillance resistance and censorship resistance.
It works by only partially disclosing the target destination, making the message go out to a number of nodes such that the target recipient cannot be singled out. However, only the target recipient can actually decrypt the message.
Substratum has used this technique to penetrate China’s Great Firewall. The platform splits transmitted data into several parts and forwards them via nodes, using artificial intelligence to find the fastest routes. Combined with encryption, this creates a secure and uncensorable connection without using VPNs or Tor.
“Our plan is to implement a term we call masquerading. We encrypt and wrap data into transactions that look similar to other patterns of web traffic,” explains Justin Tabb, the CEO of Substratum. “As we move further we will have more and more masqueraders in the hopes of never being identifiable.
”Putting this system on the blockchain actually plays a crucial role. Eventually, VPN hosts are limited and costly. Tor is free of charge but the only incentive for anyone to use it would be anonymity. Blockchain, on the other hand, flips the entire equation. Here, the nodes can actually earn income by sharing their network.
For instance, Substratum implements a model where you pay for content based on “clicks.” This decentralized version of the web empowers the nodes instead of the centralized players and has the potential to bring net neutrality back.Hackers circumvent these techniques, or even worse, use them in their own favor?
Of course. Just as they can do with many other systems—even centralized ones. The most important takeaway is that security is a process. Blockchain is not good or evil. It can be used for both.
But it is a step in the right direction.I'm a developer and freelance tech blogger interested in cyber-security, AI and blockchain, and try to separate signal from noise in the industry.-
By
 Admin
Admin - 0 comments
- 1 like
- Like
- Share
-
By
-
As the number of sensors in vehicles, factory machinery, buildings and city infrastructure grows, companies are looking for a secure and automated way of enabling a mesh network for transactional processes. Blockchain appears to best fit that bill.
The total number of connected Internet of Things (IoT) sensors and devices is expected to leap from 21 billion this year to 50 billion by 2022, according to recent data from Juniper Research.
[ Further reading: What is blockchain? The most disruptive tech in decades ]
The massive growth in IoT connected devices over the next four years, Juniper claims, is driven mainly by edge computingservices – the processing of data away from the cloud and closer to the source.
A substantial portion of the estimated 46 billion industrial and enterprise devices connected in 2023 will rely on edge computing, Juniper said, so addressing key challenges around standardization and deployment will be crucial.
Blockchain, the electronic, distributed ledger technology (DLT) that also contains a business automation software component – known as self-executing "smart contracts" – could offer a standardized method for accelerating data exchange and enabling processes between IoT devices by removing the middleman. That middleman: a server that acts as the central communication spoke for requests and other traffic among IoT devices on a network.
IT INSIGHTS
What is blockchain technology?
"Fundamentally, the idea is you don't have a central agent – no one approving and validating every single transaction. Instead, you have distributed nodes that participate in validating every transaction in the network," said Mario Milicevic, a member of the Institute of Electrical and Electronics Engineers (IEEE), a leading authority on technology innovation that has more than 500,000 members.
Making a better supply chain
In a traditional supply chain setting, Milicevic explained, a central server authenticates the movement of goods and materials from one location to another. Or a central authority could decide to halt certain processes based on pre-determined rules. In a distributed blockchain IoT network, the IoT devices on a peer-to-peer, mesh network could authenticate transactions and execute transactions based on pre-determined rules – without a central server.
Blockchain technology could also improve security through decentralized interaction and data exchange by bringing scalable, distributed security and trust to IoT devices, applications and platforms. The technology uses hashing algorithms to create an unchangeable record of transactions, and that information can be encrypted and only accessed through public and private keys.
Smart contract software, self-executing code that could be embedded on each IoT chip, could determine what action takes place when a condition is met. Those actions would only be executed when an incoming transaction authenticated.
"So, you don't need central agency to tell each node when to do something," Milicevic said.
SponsoredPost Sponsored by SAS
Images of deforestation can fight climate change
A Brazilian information society expert shares how the power of data can advance the social good.
Blockchain ledgers decrease the time required to complete IoT device information exchange and processing time."It could be in an automotive manufacturing plant.
As soon as a certain part arrives, that part then communicates that to other nodes at that destination, which would agree that part arrived and communicate that to entire network. The new node would then be allowed to begin doing its work," Milicevic said.
The rise of edge computing is critical in scaling up tech deployments, owing to reduced bandwidth requirements, faster application response times and improvements in data security, according to Juniper research.Blockchain experts from IEEE believe that when blockchain and IoT are combined they can actually transform vertical industries.
While financial services and insurance companies are currently at the forefront of blockchain development and deployment, transportation, government and utilities sectors are now engaging more due to the heavy focus on process efficiency, supply chain and logistics opportunities, said David Furlonger, a Gartner vice president and research fellow.
For example, pharaceuticals are required by law to be shipped and stored in temperature-controlled conditions, and data about that process is required for regulatory compliance. The process for tracking drug shipments, however, is highly fragmented. Many pharmaceutical companies pay supply chain aggregators to collect the data along the journey to meet the regulatory standards.
Last year, SAP partnered with IBM to demo how IoT and blockchain could automate a pharmaceutical supply chain for both tracking and reporting purposes. SAP combined its Leonardo IoT software platform with IBM's blockchain cloud service to create a working model of a system that could track and manage pharma supply chains using smart contract rules.One misconception about blockchain, is that it replaces legacy systems.
"In fact, blockchain is a layer on top of enterprise applications."
BrandPost Sponsored by Huawei
How banks are looking to their foundations to take digital leadershipThere is fierce technology-driven competition in the financial sector. What is driving this trend, and what are banks doing to meet the evolving needs of customers via digital platforms?
SAP also recently completed two proof-of-concept (PoC) blockchain deployments with customers: one was a smaller supply chain test evaluating millions of transactions on a Hyperledger blockchain using smart contract technology in IoT devices; the second was a much larger one that represented billions of transactions among 15 different customers using MultiChain open-source blockchain software without smart contract code on the devices.
The smaller PoC with smart-contract technology worked well, but was more expensive to set up because it required a blockchain developer – someone that's in short supply – to write the code, said Gil Perez, head of Digital Customer Initiatives for SAP.
"In the small pilot, the cost of operations and overhead was rather high. So, functionally it exceeded expectations, but from financial perspective it was very challenging," Perez said.
The second PoC addressed both scalability and cost, in that it proved the blockchain could scale to enterprise levels and didn't require a developer to write smart contract code for the IoT devices; instead the business automation ran on servers separate from the blockchain.
The MultiChain PoC was not as efficient as the Hyperledger model, but it cost less and it met the busienss requirements, Perez said. He added that the smaller PoC required more complex logic in the form of smart-contract code on IoT devices.
"The fact that you put the logic on a server doesn’t mean it's not automated," Perez said, referring to the larger PoC. "We have the flexibility to put the logic in different places. The deployment and business use cases need to consider not only the technological capabilties but the business and commercial implications."
SAP has been working with about 65 of its customers to develop blockchain augmented software – something Perez said will soon be available."It just becomes a part of the upgrade cycle. It’s built into the standard software SAP provides them," Perez said. "If SAP has a standard application and we add the capability to extend or augment the application for blockchain capabilities, we believe it will help also accelerate the adoption of blockchain.
At its Sapphire Conference in May, SAP announced a blockchain cloud service for its customers -- something that's also becoming a popular option for companies that don't want to expend capital in order to test distributed ledger technology.
IBM also recently launched an IoT-to-blockchain service as an add-on to its existing IoT Connection Service. It enables IoT devices, such as RFID location chips, barcode scans or device-reported data, to be transmitted to a permissioned blockchain on IBM's cloud service. That blockchain-based network can then be used by a business network of computers to validate provenance.
Devices able to communicate data to blockchain ledgers can update or validate smart contracts. For example, as an IoT-connected shipment of goods moves along multiple distribution points, the package location and temperature information could be updated on a blockchain. This allows all parties to share information and status of the package as it moves among multiple parties to ensure the terms of a contract are met, according to IBM.
SAPNew uses for blockchain will continue grow because of the DLT's ability to provide new forms of security, according to B2B reviews platform G2 Crowd."Information security and corporate integrity have both taken a blow after events like the Equifax catastrophe, and companies are investing in blockchain as a precaution," G2 Crowd said in a report.
Blockchain enables secure access to IoT sensors
For example, global wireless network technology provider ABB Wireless adopted blockchain as a method for delivering decentralized security services for industrial systems in industries such as utilities, oil and gas, and transportation.
Cybersecurity for IoT is becoming more relevant as industries transition into the age of "smart" systems, which use tiny electronic devices to communicate with, and control, everything from building HVACs to international cargo shipments.
ABB Wireless is using a blockchain platform developed by Xage, a startup that officially launched earlier this month.ABB Wireless used Xage's security application running on edge gateways within a number of components at power utility substations. The mesh network enables secure, remote access to IoT devices to control the substations, allowing for everything from viewing maintenance data to rerouting power.
On a system with thousands or tens of thousands of IoT nodes, the possibility of hacking the network is remote at best."If you add a million more smart meters to a wireless network, you've just made that network harder to hack. Whereas in a traditional network, the more units you add, the more exposure there is to hacking," said Xage CEO Duncan Greatwood.
The blockchain app contains an encrypted and immutable table of security credentials, which allows field workers to log into a device – even if the substation is disconnected from a utilities' central data center due to an accident, such as a wildfire.
"Everyone's scared to death that someone is going to get control of the grid," said Paul Gordon, vice president of engineering and operations at ABB Wireless. "This provides a solution in a scalable way, so security doesn't become a huge burden. It allows for a more scalable solution while meeting needs of highly secured environment."
Combining the immutability of a blockchain distributed ledger with encryption means that the more end nodes that are added, the more secure the network becomes, unlike traditional relational database systems that have a single point of access. Blockchain-on-IoT devices are more secure because a cyber attacker would need to break into a majority of the nodes to gain controllable access to a system.
Blockchain is under-researched; CIOs remain cautious
Blockchain itself is still a wildly understudied technology. In an IEEE database of 40 million research papers, only 480 contain the term "blockchain," said Milicevic, who is a staff communication systems engineer at MaxLinear, a provider of high-performance broadband and networking semiconductor products.
[ Related: The top 5 problems with blockchain ]"
There is research, but it's at a very high level from what I've seen. I haven't seen anything really deep," Milcevic said.Many of the high-level level articles in the IEEE database are focused on potential applications, with many of those mentioning IoT networks and how a marriage with blockchain could improve supply chains.
There are, however, "very few examples" of real-world blockchain networks that have been deployed; that kind of information could provide businesses with data about the number of nodes, power consumption, and the efficiency of an IoT network before and after blockchain was deployed.
It would also offer examples of project failures, Milcevic said."We don't understand the cost or the security issues, such as what would happen if rogue nodes could overtake the network. Today, you still have a centralized authority that can shut the network down," Milcevic said.
"In decentralized network there is no central authority. I've yet to see a hard study on that. I think everyone is waiting to see what everyone else does. That's the challenge. No one really knows what everyone else is doing."
When there's no central authority and only a mesh network of automated nodes, it's scary," Milicevic said.For example, an IoT sensor manufacturer could place security backdoors in the device software that could be activated with a trojan horse or a virus.
"In fact, someone may have paid me as an employee of that company to install a back door that may allow me to come into your network without you knowing," Milcevic said. "If you're able to have more than 50% of computing power controlled in rogue nodes then the entire history of the blockchain could be overwritten with whatever you want."
One strength of a blockchain ledger, however, is that it cannot be overwritten; it is a write-once, append-many technology. So, the history of all transactions on the peer-to-peer network remains regardless of any intrusion.The lack of real world examples of blockchain deployments is one reason C-level executives are cautious about embracing the technology.
A recent survey of CIOs by Gartner highlighted that trend. Only 1% of the CIOs indicated any kind of blockchain adoption within their organizations, and only 8% said they were in short-term planning or active experimentation with blockchain, according to Gartner's 2018 CIO Survey.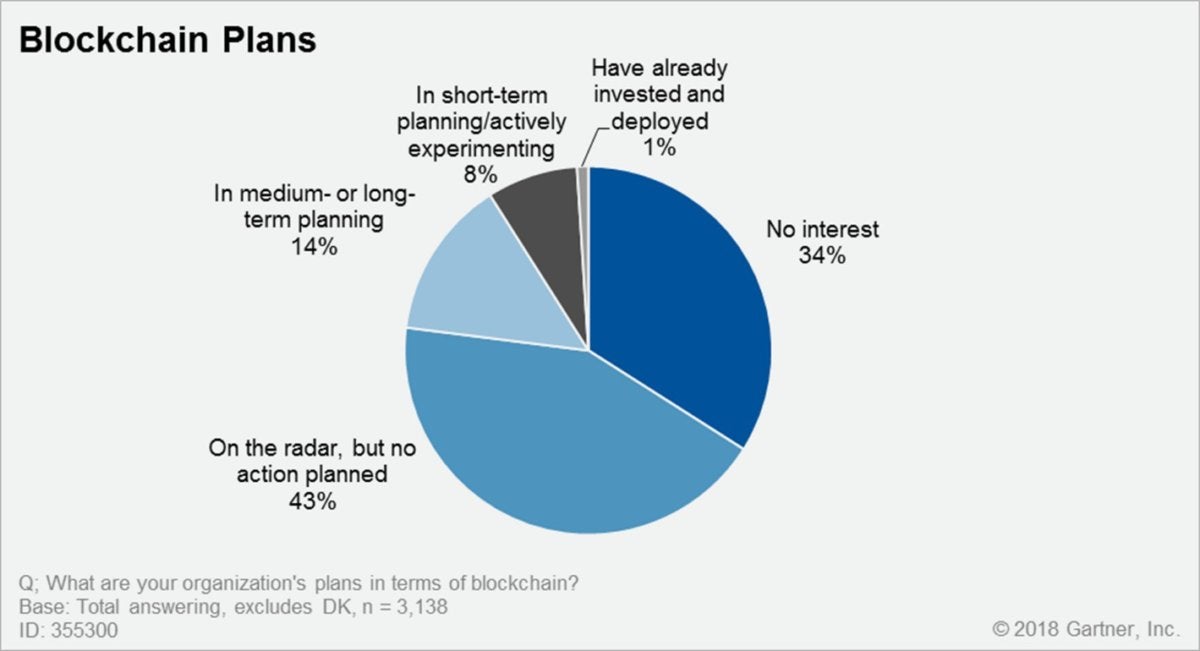
Gartner"This year's Gartner CIO Survey provides factual evidence about the massively hyped state of blockchain adoption and deployment," said Furlonger. "It is critical to understand what blockchain is and what it is capable of today, compared to how it will transform companies, industries and society tomorrow."-
By
 Admin
Admin - 0 comments
- 2 likes
- Like
- Share
-
By
-
Everything you need to know about hot wallets, cold storage and seed phrases.
One of the hallmark qualities of cryptocurrency is its virtuality. Unlike most other forms of currency, crypto has no physical embodiment. You can't get it as paper, coin, bar of gold or fancy bead. There's no token that needs to be locked up in a bank vault or buried beneath a mattress.But like anything valuable, cryptocurrency needs to be protected.
It exists as a natively digital entity that requires an internet connection for any transaction -- and that connectedness makes it vulnerable to hacking. In fact, despite its ethereal nature, it's at least as susceptible to plunder as cash or gold. And with cryptocurrency, these violations are likely to come remotely.
Read: Bitcoin explained -- everything you need to know
Exchanges' default wallets are risky
Many newcomers buy cryptocurrency from an exchange, such as Coinbase or BitFlyer, and leave their holdings in those sites' "custodial" wallets. But like any other online entity, the exchanges are vulnerable to hacking -- and as the crossroads for many billions of dollars of transactions every day, they make for particularly attractive targets.
The cautionary tales of Mt. Gox, which "lost" 750,000 of its customers' bitcoins in 2014; NiceHash, which was robbed of $60 million in December 2017; and a recent close call at Binance show the risks associated with leaving your coins in an exchange's online wallet.
Cold storage vs. hot wallets
Conventional wisdom dictates that if you've got more virtual currency than you'd be comfortable carrying around on your person, or you intend to hold it as a long-term investment, you should keep it in "cold storage." This could be a computer that's disconnected from the internet or a specialized USB drive called a hardware wallet. (We'll take a look at how those work in a future explainer.)
Dedicating a computer to store your cryptocurrency or shelling out for a hardware wallet isn't an option for everyone, however. Well known devices such as the Trezor and Ledger cost between $75 and $100 and, by design, add complexity and a few extra steps to every transaction. Software wallets, by contrast, are usually free and easily accessed though, ultimately, less secure.
Three kinds of software wallets
A cryptocurrency wallet's primary function is to store the public and private keys you need to conduct a transaction on the blockchain. Many also offer features such as integrated currency swapping. There are three main kinds of software wallets -- desktop, online and mobile -- and each offers a different combination of convenience and security. Desktop wallets are software you install on your computer.
They give you lots of control over your assets but, if connected to the internet, remain vulnerable. A malware infection, the remote takeover of your computer or -- even if you're not online -- a hard-drive failure could be a catastrophe.
Read: Blockchain Decoded on CNET
Online wallets are hosted on a website. This makes them convenient because they're accessible from any internet-connected device. The downside: Your private keys are (theoretically) known to the website owner and, from a technical perspective, there's not much to stop them from simply taking your coins.
Mobile app wallets are optimized for retail transactions -- that is, paying for stuff with bitcoin or another cryptocurrency. But because your encryption keys are stored on your phone, you lose your coins if you lose your device. You thought it was a bummer to leave your phone in a taxi? Imagine how bad it will be if it has thousands of dollars of cryptocurrency locked on it.
28 things you didn't know you could buy with bitcoins
Security fundamentals
Whether you choose a hardware, software or paper wallet to manage your passwords and private keys, there are a handful of things you can do to keep your stash safer. These include:
Be super careful with any online service -- any device connected to the internet is vulnerable Encrypt your wallet with a strong passwordMake regular backups and store them in multiple locationsUse multisignature security, which helps maintain control of your coins even if one of your devices is compromisedGenerate, write down and hide your wallet's mnemonic seed -- a group of words you can use to restore your wallet in the event of a hardware failure
Some software wallet options
We'll take a high-level view of some well known software wallets to provide an overview of the different features and tradeoffs to consider. Note: There are many wallet options available, and we have not comprehensively tested any of these. As such, we cannot recommend any of them. As with everything related to cryptocurrency, you are advised to do your own research before making any decisions. Caveat emptor!
Jaxx
JaxxA versatile online wallet, Jaxx can be installed on a computer (Windows, Mac or Linux), added as an extension to the Chrome web browser, or downloaded as an app on an Android or Apple phone or tablet. In addition to helping you store dozens of cryptocurrencies, Jaxx's support for the ShapeShift API makes it easy to swap coins -- say, Litecoin for Ether -- right inside the wallet.
ShapeShift's exchange rates aren't always as low as what you'll find on major exchanges and they do charge a transaction fee (or "miner fee"), which was about 40 cents on the Bitcoin to Ether transaction we priced out. Jaxx offers novices an easy pathway into alt-coins that aren't yet supported by Coinbase or Bittrex.Learn more: jaxx.io
MetaMask
Super simple to install and use, MetaMask is a specialist, supporting only ERC20tokens -- that is, any cryptocurrency built on the Ethereum platform. The good news: there are about 50,000 or so tokens (and projects) built on Ethereum, accounting for roughly 90 percent of the total cryptocurrency market cap, which was more than $200 billion at the time of writing, according to CoinMarketCap.com.
MetaMaskMetaMask can be used to send, receive and store Ethereum tokens and private keys. All of the data is encrypted and stored locally, making it difficult for the developers or anyone else to steal your keys or coins remotely. And, in addition to its storage and transactional capabilities, the MetaMask extension connects most web browsers (Chrome, Firefox, Opera and Brave) with the growing universe of decentralized applications, also known as dApps, being built on the Ethereum platform.Learn more: metamask.io
Exodus.io
The Exodus software wallet is a good entry-level wallet for cryptocurrency newcomers. It's known for responsive customer support, copious user documentation and a refined design and interface. It accommodates dozens of coins (here's a full list) and was the first wallet to support Shapeshift. There's no mobile app yet, however, and Exodus doesn't offer two-factor authentication or multisignature addressing, which gives you the power to require approval from multiple devices before finalizing a transaction. This could give security-minded coin owners pause. Learn more: exodus.io
Mycelium
One of the first mobile wallets, Mycelium has since established a solid reputation as a secure and user-friendly way to store bitcoin (and, so far, only bitcoin). Like any credible wallet, it lets you generate a set of 12 "seed words" that will help you restore the wallet if you lose access to your private keys.
There's no desktop interface, but it can be used in tandem with a cold storage solution, managing your accounts on a hardware device like a Trezor or Ledger. (The company also produces a USB key that generates paper wallets; plug it into your printer and out comes a paper wallet without any need for a computer.)
Mycelium Instead of using ShapeShifter, Mycelium runs its own reputation-based exchange platform, which helps coordinate bitcoin trades between buyers and sellers. Transactions incur a fee that ranges from about 70 cents to $8 depending on the priority you set -- that is, how quickly you want it to be confirmed and added to the blockchain. Learn more: wallet.mycelium.com
Remember: Do your own research before installing or using any of these wallet technologies -- or trading or investing in any cryptocurrency.
Buying and selling bitcoin: A quick and dirty introduction to trading cryptocurrency.
Initial coin offerings, explained: How can this possibly be a legitimate way to raise money?
Cnet is is one of the leading publishers of technology over the last 2 decades. Discover more from Cnet here: https://www.cnet.com/how-to/how-to-keep-your-cryptocurrency-safe/-
Francisco Gimeno - BC Analyst With #crypto came the wallets. These wallets have two big issues: security and use at this stage. With the #ecosystem's evolution, also crypto wallets will have to change into a more safe, secure and easier to use wallet. Here we find some ideas and examples. Have you got these issues too? What do you think?
-
-
The future is fast approaching in the form of smart cities. But at the same time, a global horde of hackers are close behind, ready to exploit the weakest links.
Smart cities can reduce resource consumption, using IoT devices to optimize the use of electricity and water; reduce traffic congestion and air pollution through smart coordination of traffic lights, parking availability, and public transportation; and harness the power of big data and ubiquitous IoT devices to enhance the efficiency and livability of the urban environment.
Technology research firm Gartner estimates there were already some 2.3 billion connected devices within cities around the world by the end of 2017, more than a 40 percent increase over the year before.
But the more IoT sensors that are deployed, the greater is a city’s attack surface for hackers and other bad actors. And so far, cities — and the rest of the IoT industry — haven’t done a very good job of implementing security.
The threats could lead to lethal chaos — a hacker maliciously tampering with traffic lights; industrial mayhem through hacking of municipal power, water, or sewage systems; financial loss, for example through theft of electrical power; and a spectrum of other vulnerabilities.
This increased attention to IoT security is a welcome sign. For years, it was all but ignored for two closely related reasons: on one hand, IoT devices are so small, many think, why bother? On the other hand, IoT devices have proven to be extremely difficult to secure simply because they are so small — especially when it comes to the size of RAM and storage.
Traditionally, security teams have had enough problems in securing full-stack servers sitting behind firewalls. Now that the world is waking to the immense threatscape posed by billions of unsecured and poorly secured IoT devices — hanging from power poles, mounted on buildings, bolted to heavy equipment — we face the daunting challenge of protecting devices with RAM and storage that are measured in kilobytes — not megabytes and gigabytes.
Traditional security stacks — which are comprised of multiple layers of cybersecurity infrastructure — simply won’t fit onto IoT devices. In fact, while we refer to devices as being part of the internet of things, few actually have room for the most fundamental layer, otherwise known as the IP stack, which allows them to directly connect to the internet, hence the reliance on wireless connectivity.
Using blockchain, which is the secure, decentralized mechanism behind cryptocurrency, we have an opportunity to bring connectivity to scale without compromising security in the process.
While IoT devices themselves lack the resources to host a blockchain, the immutability of the system coupled with cryptographic keys can be used to establish root identity for devices.
Devices can present credentials to participate within an IoT environment, with these credentials stored to — and later validated from — a public blockchain such as Ethereum.Add some machine learning algorithms, and you can track device reputation and behavioral variations that can signal departure from pre-set attributes and norms. Identity and reputation are foundational to securing the IoT.
In this manner devices can engage in secure autonomous transactions within a sphere of trust. And to really be safe, all data collected by an IoT device should be encrypted to remove reliance on transport-layer protection.
Blockchain also offers powerful ledgering and audit capabilities through its inherent timestamp function.
Whether opening a water valve or dispensing medication through an IV drip, whenever blockchain is involved you have a precise, and immutable, record of the event.In addition to blockchain, we need precision coding. In the early days of coin-operated video games, developers worked in machine code as they sometimes had only 6k of ROM storage.
Similar skill is required to craft an efficient IoT security stack today that must fit within perhaps a 256kB ROM chip and operate with as little as 128kB of RAM — while also leaving room for the device’s operating system and application code.
This combination of blockchain technology and precision coding can go a long ways toward providing the heavyweight security required to protect the lightweight IoT devices that will enable smart cities.
Vaughan Emery is the founder rand CEO of Atonomi, a blockchain-based arm of CENTRI technology, a firm that provides security for the internet of things.
Did You Know About This?
You can curate a Personal Blockchain Page right here on Blockchain Company ( BC ) like these 2 great user examples here:
http://www.blockchaincompany.info/Paula
http://www.blockchaincompany.info/Francisco
Show your blockchain page of to your employer, colleagues and friends. It demonstrates your professional awareness and competency of this revolutionary paradigm changing the world. It's free if you are a consumer user. Just Create your Account here in less than 3 mins!
Or Click Create Account above in the upper right corner. Instructions how to curate your blockchain page from information you discover on BC, is sent in your email after you sign up.
You might be able to capture your ' first name " unique url for your blockchain page too! Like : http://www.blockchaincompany.info/robert
You may be entitled to cryptocurrency tokens, airdrops, offers and discounts at any time in the future once you are a user on our platform.
-
Francisco Gimeno - BC Analyst Interesting Use Case on #thehill. Blockchain could help to fight against cyber crimes by protecting IoT devices that will enable smart cities in the next future.
-
-
Is blockchain -- the network of global online ledgers -- really secure? Its proponents say yes, as it assigns transactions or smart contracts to an immutable ledger, verifiable by multiple parties.
However, a recently published paper calls out some vulnerabilities that may subject blockchain entries to inefficiencies, hacking and other criminal
activity.
Photo: Joe McKendrickThe paper, published by Xiaoqi Li, Peng Jiang and Xiapu Luo (all with Hong Kong Polytechnic University), Ting Chen (University of Electronic Science and Technology of China), and Qiaoyan Wen (Beijing University), asserts that blockchains have several points of vulnerabilities of which users need to be aware.
As blockchain increasingly becomes part of business operations, there needs to be a closer examination of the potential security liabilities that come with this emerging technology. With the growth of the number of decentalized applications, "the privacy leakage risk of blockchain will be more serious," Li and his co-authors state.
"A decentralized application itself, as well as the process of communication between the app and Internet, are both faced with privacy leakage risks." They urge greater adoption of techniques to address the challenge: "code obfuscation, application hardening and execution trusted computing.
"The researchers outline key known risk factors with blockchain:
Blockchain efficiency: For starters, he efficiency of blockchains themselves may become overloaded with complex consensus mechanisms and invalid data. Li and his co-authors note that the consensus mechanisms employed across the Internet are computing resource hogs.
For instance, most popular consensus mechanism used in blockchain is Proof of Work, which the researchers call a "waste of computing resources." They say there are efforts to develop more efficient and hybrid consensus mechanisms that combine PoW and Proof of Stake (PoS).
In addition, blockchains will produce a lot of data -- block information, transaction data, contract bytecode -- that may be outdated and useless. "There are a lot of smart contracts containing no code or totally the same code in Ethereum, and many smart contracts are never be executed after its deployment.
An efficient data cleanup and detection mechanism is desired to improve the execution efficiency of blockchain systems."
"51% vulnerability:" Blockchain "relies on the distributed consensus mechanism to establish mutual trust.
However, the consensus mechanism itself has 51% vulnerability, which can be exploited by attackers to control the entire blockchain.
More precisely, in PoW-based blockchains, if a single miner's hashing power accounts for more than 50% of the total hashing power of the entire blockchain, then the 51% attack may be launched.
Hence, the mining power concentrating in a few mining pools may result in the fears of an inadvertent situation,such as a single pool controls more than half of all computing power.
"Private key security: "When using blockchain, the user's private key is regarded as the identity and security credential, which is generated and maintained by the user instead of third-party agencies. For example, when creating a cold storage wallet in Bitcoin blockchain, the user must import his/her private key.
" An attacker could "recover the user's private key because it does not generate enough randomness during the signature process.Once the user's private key is lost, it will not be able to be recovered.
Since the blockchain is not dependent on any centralized third-party trusted institutions, if the user's private key is stolen, it is difficult to track the criminal's behaviors and recover the modified blockchain information."
Criminal activity. "Through some third-party trading platforms that support Bitcoin, users can buy or sell any product.
Since this process is anonymous, it is hard to track user behaviors, let alone subject to legal sanctions." Frequent criminal activities with Bitcoin include ransomware, underground markets and money laundering.
Double spending. "Although the consensus mechanism of blockchain can validate transactions, it is still impossible to avoid double spending, or using the same cryptocurrency multiple times for transactions. The attacker can exploit the intermediate time between two transactions' initiation and confirmation to quickly launch an attack.
"Transaction privacy leakage. "Unfortunately, the privacy protection measures in blockchain are not very robust," Li and his co-authors state. "Criminal smart contracts can facilitate the leakage of confidential information, theft of cryptographic keys, and various real-world crimes (e.g.,murder, arson, terrorism, etc.)
"Vulnerabilities in smart contracts.
"As programs running in the blockchain, smart contracts may have security vulnerabilities caused by program defects." For example, one study found that 8,833 out of 19,366 Ethereum smart contracts are vulnerable to bugs such as transaction-ordering dependence, timestamp dependence, .
mishandled exceptions, and .re-entrancy vulnerability.
"Under-optimized smart contracts: "When a user interacts with a smart contract deployed in Ethereum, a certain amount of "gas" is charged. Gas can be exchanged with "Ether," which is the cryptocurrency in Ethereum.
This results in "useless-code related patterns," and "loop-related patterns." This consists of "dead code, opaque predicate, and expensive operations in a loop.
"Under-priced operations: "Ethereum sets the gas value based on the execution time, bandwidth, memory occupancy and other parameters. In general, the gas value is proportional to the computing resources consumed by the operation.
However, it is difficult to accurately measure the consumption of computing resources of an individual operation,and therefore some gas values are not set properly. For example, some IO-heavy operations'gas values are set too low, and hence these operations can be executed in quantity in one transaction.
In this way, an attacker can initiate a Denial of Service attack on Ethereum."
Learn more like this from Znet here: http://www.zdnet.com/article/9-reasons-to-be-cautious-with-blockchain/-
Francisco Gimeno - BC Analyst As a new technology, Blockchain growing problems also show some suggestions of vulnerabilities which must be tackled on and solved. Interesting report here on this issue. Take care.
-






